nep
;)
留校的时候打的,感觉特别高脂,复现一下
realme
这道题当时用ida写的,现在看到很多wp都是用dbg
首先有调试,用dbg的插件去调试,真的很方便●﹏●
可以看到密钥和输入都被push了进入加密,过加密之后直接dump
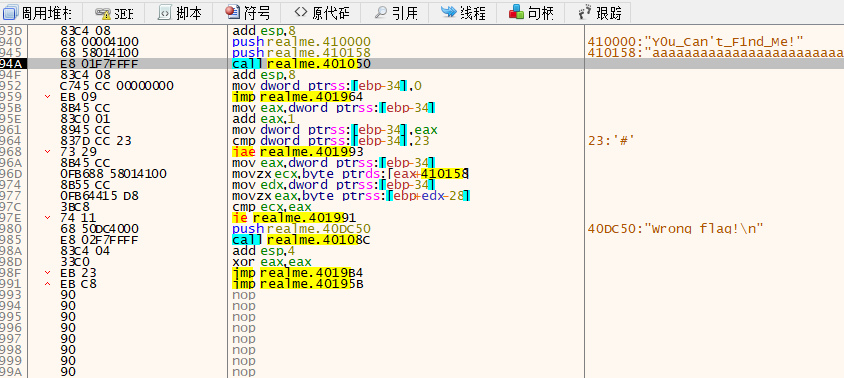
然后再ida打开,会发现加密过程变成了真的不是原来的假的
1 | #include <stdio.h> |
SMC
其实我对它的理解一直停留在新生赛,VirtualProtect一函数为标志,现在有了新的理解
它是可执行文件中的指定区段实施加密处理,SMC 技术会将那些需要加密的代码部分,诸如特定函数或代码块等,单独编译成独立的 section(段)。
所以这个程序中的section可以看见rc4在自定义段

代码段改为可读可写可执行的,此时代码段就可以被视作数据段,即能够进行正常数据操作,从而对代码的硬编码做一个修改
Crack me
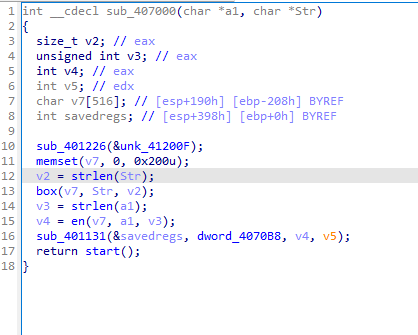
主函数挺容易找的,输入32位十六进制变成了16位的字节
动调可以发现sign函数和AES加密
两次sign里输入的不一样,第一次是用户名,第二次是用户名+Showmaker11
然后获得两个签名
大概的验证意思就是
用户输入的 16 字节和 sign(username + “Showmaker11”) 结合,用 AES 处理
如果 sign(username) 对应就是正确的
输入是16个字节,AES-128,仔细分析一下AES可以发现
字节代换没有变化,s盒没被魔改,
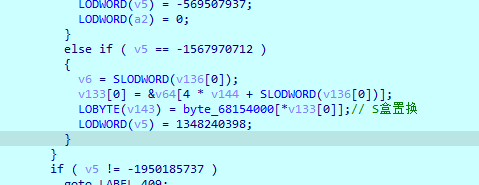
行位移
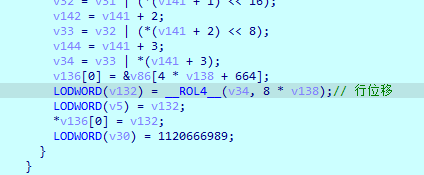
列混淆 多了一个异或0x55
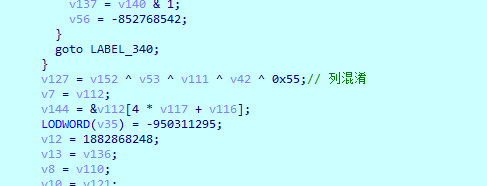
密钥扩展
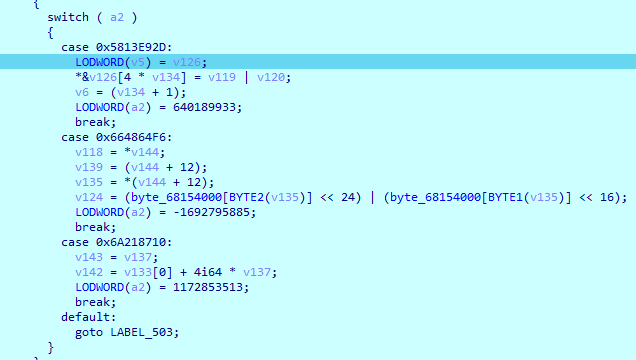
轮密钥加
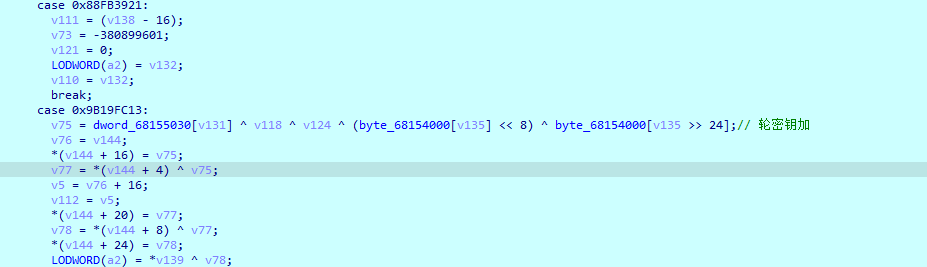
轮数任然是AES-128的10轮
法一 动调出密文密钥
断点在AES加密的函数上,取出密钥
密文直接再v58上取
写个脚本
1 | #include <stdio.h> |
法二 调用dll
可以看出这两函数都是在libcrypto.dll中,可以直接调用
1 | #include <iostream> |
QRS
这个运行起来熟悉感扑面而来,有点像暑假的一道题
依旧打开恢复符号表,可以看出来有一些带rust的系统函数
在main函数的一开头下断点,调试不了,在GetCurrentThread引用找到了反调试的地方nop掉重新调试,但是在这里往后一直调的话找不到输入的地方,最后还是找了missing field函数引用在这下了断点
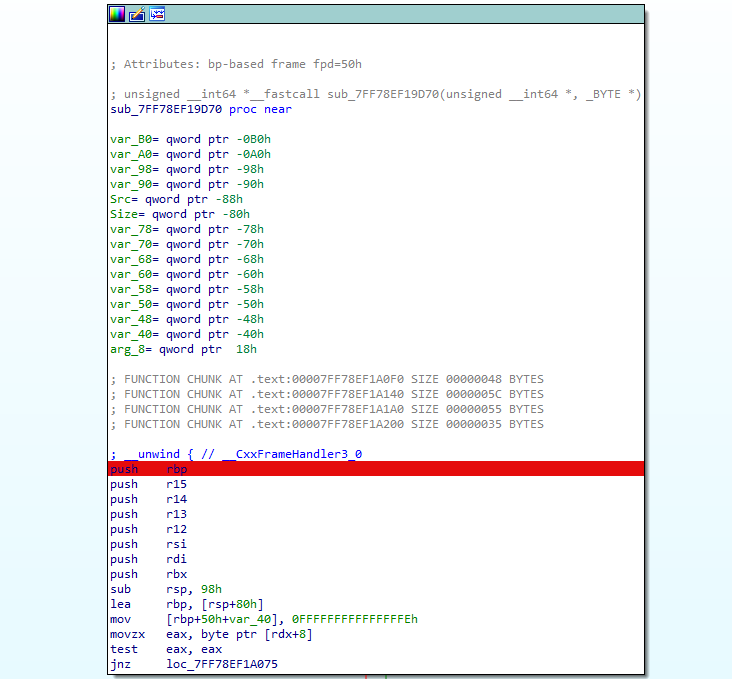
然后就调试在1970断下的地方输入,是get传参,往后调
1 | http://127.0.0.1:8887/interface?input=AAAAAAAAAAAAAAAAAA |
这里其实当时调了很久,很好奇为什么是get不是post。
暑假那道题其实题目里给了就是要求get请求。
朋友说因为post传参不会被记录到地址中,get上传的数据会被缓存,嘶很有道理
后面会碰到一个大跳那是加密的地方,在汇编可以看到我刚刚的输入,下面那个是加密函数,可以看见里面是xtea加密
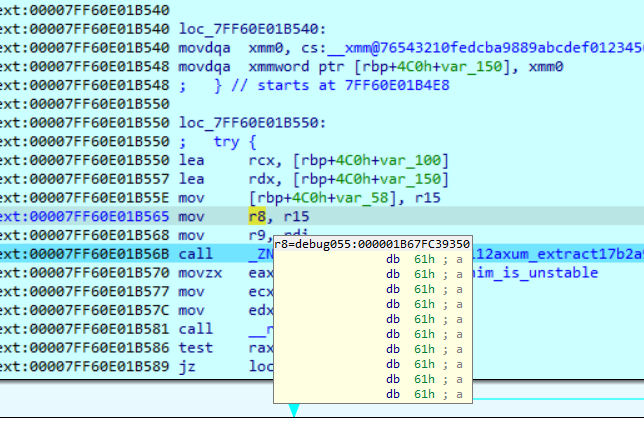
魔数可以动调看见定值,密钥和密文拿到写脚本
1 | #include <stdio.h> |
axum框架
Axum是Rust生态里的一个 异步Web 框架,类似 Go 的 net/http
FlutterPro
这道题,没办法正常解出来,报错了
ai说是libapp.so 里找不到符号 _kDartVmSnapshotData,里面是Dart 的一些东西。
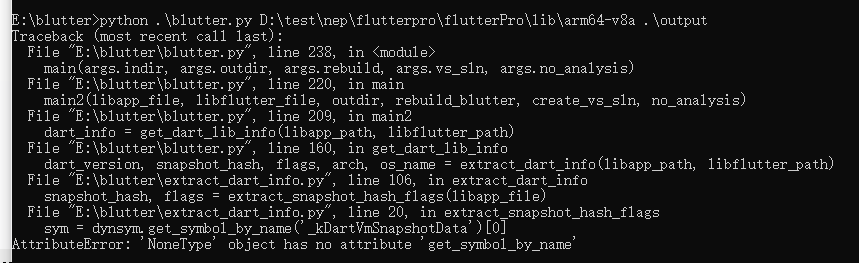
ida打开在字符串里面意外发现了 _kDartVmSnapshotData,因为到0x346的时候突然出现了一堆0,所以报错了

1 | def extract_snapshot_hash_flags(libapp_file): |
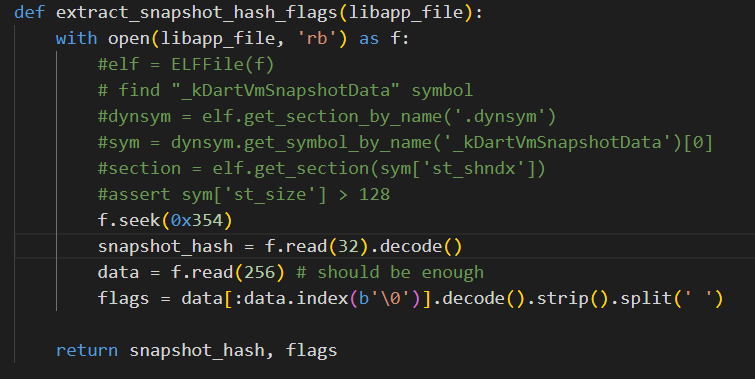
可以看到extract_dart_info里面的源码,是连续读取的我们修改一下改成从0x354开始读,然后继续尝试一下
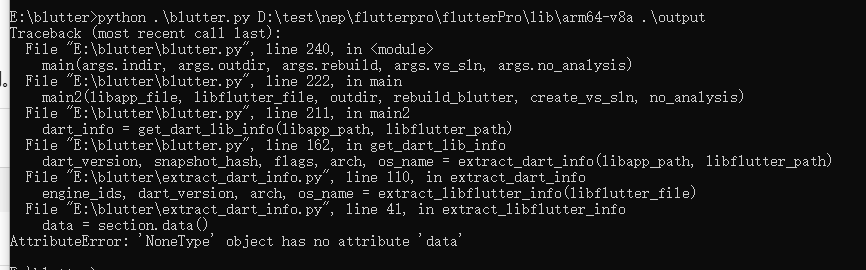
蒽依旧报错这次是因为**.rodata 段**没找到,分析一下so
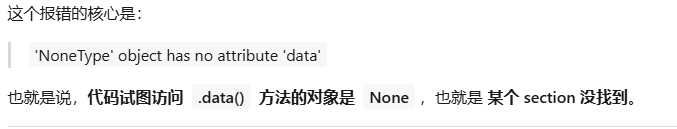
看了一下正常的.rodata、.text、.bss段都被删去了,嘶难搞再跑到源码那分析了一下找.rodata 段的代码,代码的作用是找flutter的版本信息和Dart SDK的版本号
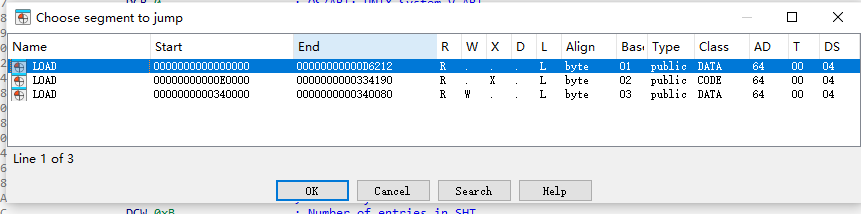
出问题的地方应该是这边
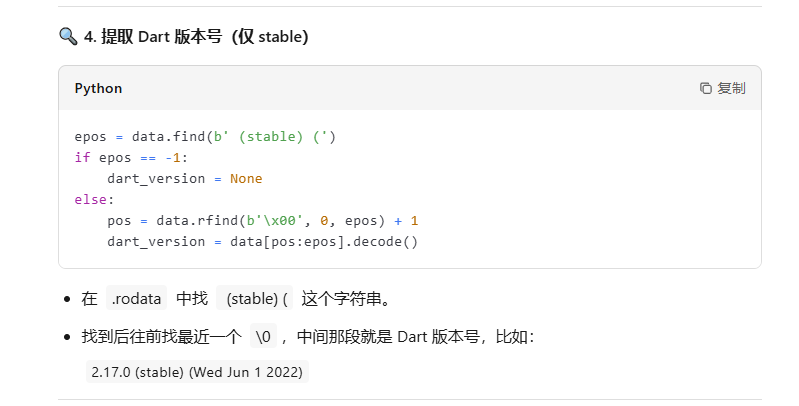

修一下,经过好久的编译错误终于成功了,在官方wp里面找到了ida9还原函数名的方法
1 | python blutter.py --dart-version 3.8.1_android_arm64 D:\test\nep\flutterpro\flutterPro\lib\arm64-v8a\libapp.so .\output |
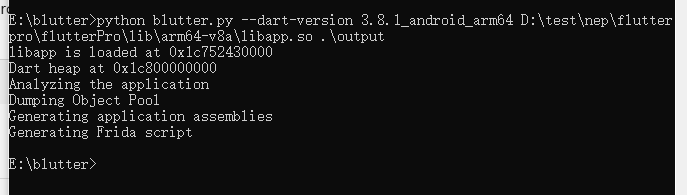
在output文件夹里面asm/flutterpro/main.dart可以看到有两个回调函数其中ontap点击事件在ida里面分析,找到主要事务函数分析
不断ai
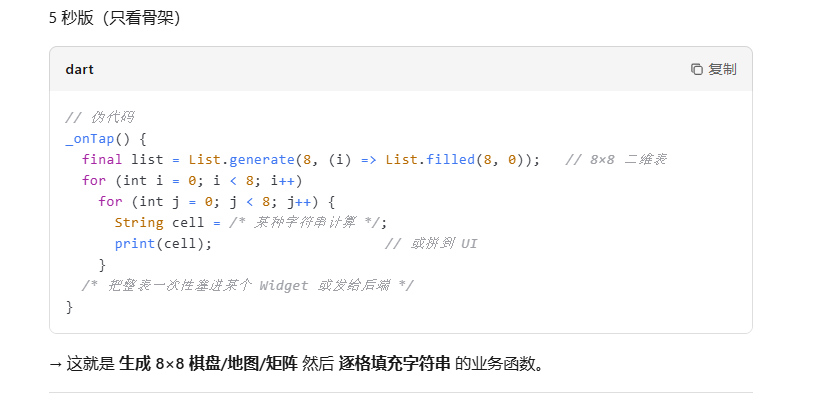
大概就是指这一部分构成一个8*8的样子,构成了之后应该会有一点操作,点进这部分下面的一个sub_203624函数继续分析,一点一点分析实在是太慢了,然后就想hook去看看,结果很久很久一直不成功,后来在一个文章里面看到要用真机😊
1 | while ( 1 ) |
在这个函数里面,可以发现是有矩阵在相乘的
我看 不论是官方的还是其它大师的wp都是hook出了矩阵的key,在blutter给的frida脚本上修改
1 | Interceptor.attach(libapp.add(0x203844), { |
所以第一次加密这边是一个矩阵相乘
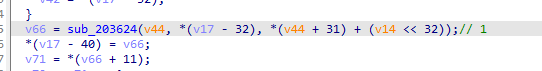
再往下分析一下
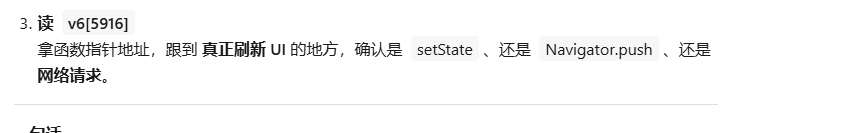
创建另一个DartObjectPool的结构体,然把v6修改成池子,变成了这样
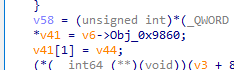
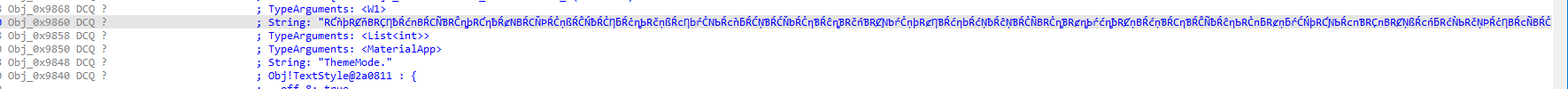
点进去就会发现又一长串的字符串,可能是密文
从相乘后往下可以发现还有一个sub_2030D8函数,点进去里面也有很多类似于v6的东西,会发现里面有写莫名其妙的字符串和密文差不多
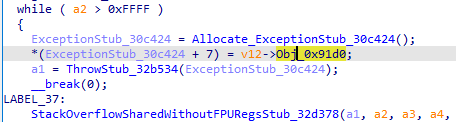
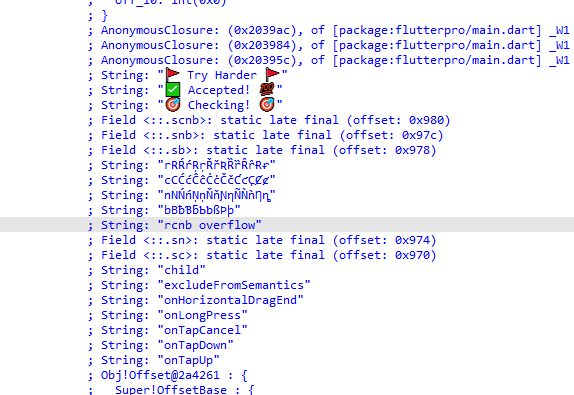
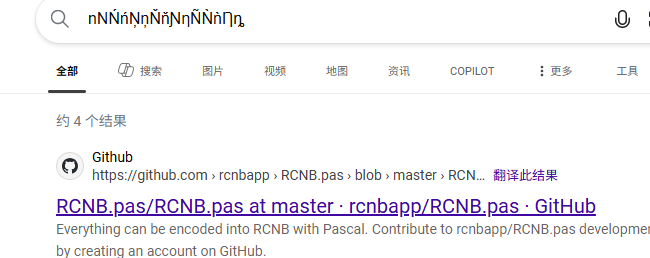
所以可能逻辑就是
input -> len -> 矩阵相乘 -> RCNB -> compare
1 | import rcnb |
1 | from z3 import Solver, Int, sat |






